March 1, 2022
Examples of Phishing

In last month’s article, I discussed various types of phishing-related messages designed to steal your personal information by criminals. Since we have continued to see an increase in phishing attempts, I wanted to include some concrete examples of what to look for in these messages.
Remember the following tips when you are trying to identify a spam message:
- Real companies will not request your sensitive information over email.
- Real companies will address you by your real name.
- Real companies know how to spell and don’t make grammar mistakes.
- Real companies don’t send unsolicited attachments.
- Real companies don’t send attachments that you did not request.
- Real companies will send you emails from their domain, not a fake address.
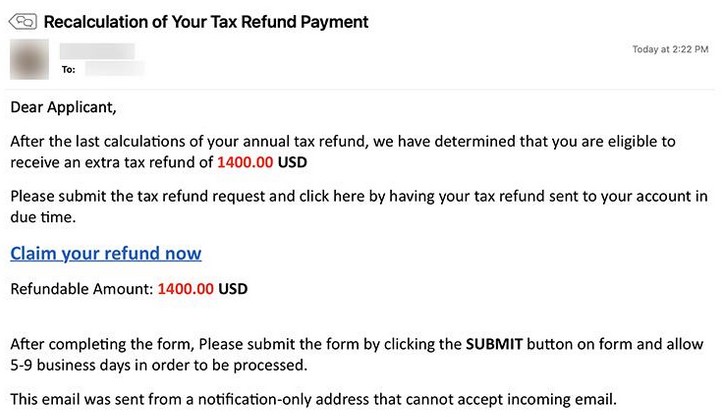
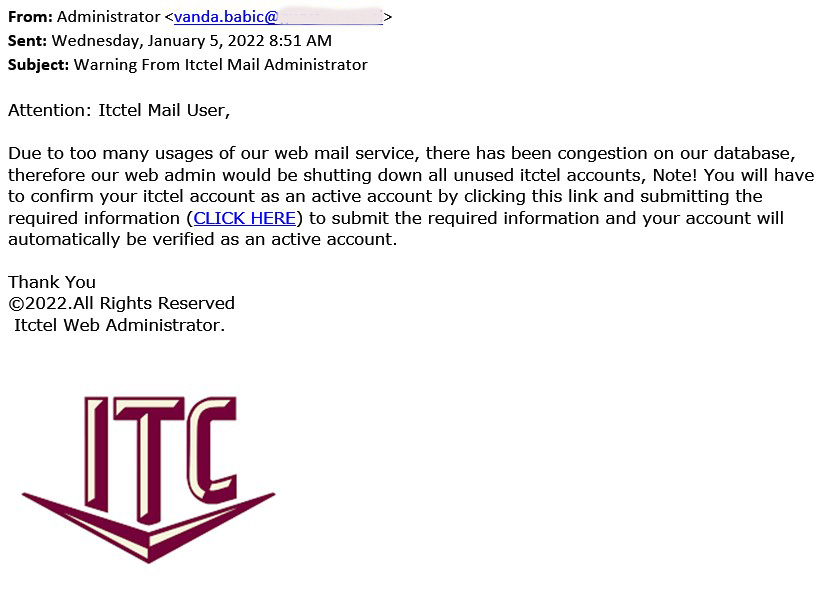
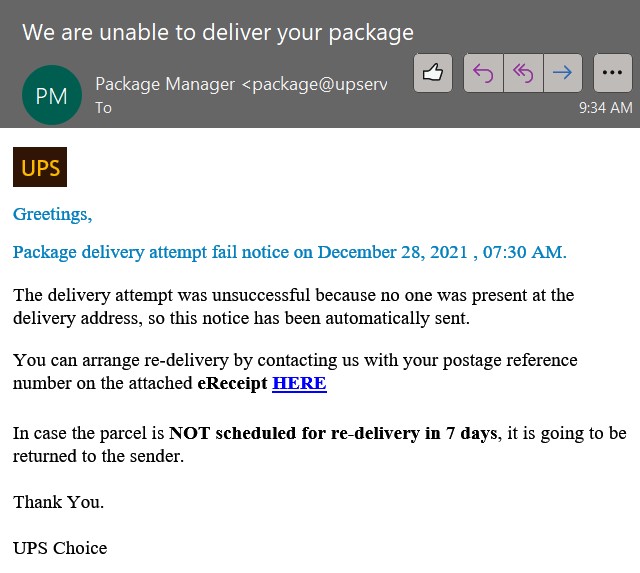
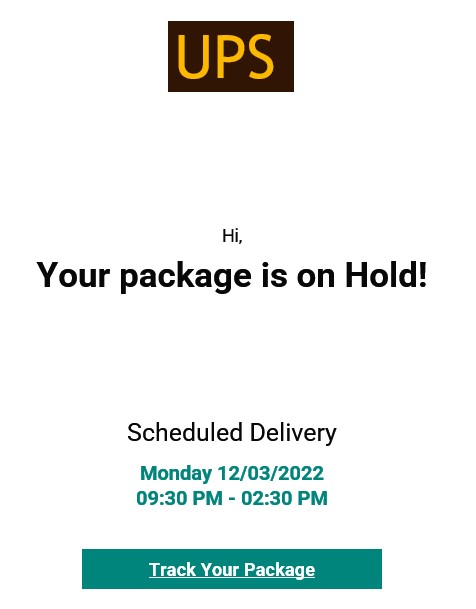
At first glance, phishing emails may appear to come from “ITC,” “UPS,” or the “IRS.” These are organizations that many people would respond to. In a UPS example, the message has a sense of urgency because something ordered is being held. Other variations say the package couldn’t be delivered, or a pickup time needs to be scheduled. In an IRS example, the scammer attempts to entice the victim with the promise of free money.
One of the first signs that an email is not legitimate is that it does not use the customer’s name. Instead, they say “Hi,” and “Dear Applicant.” Other variations of these phrases might also be used.
The email may include a link that does not go to the company, like UPS, Netflix, IRS, or other real websites. The link is usually innocent-sounding, such as “Track Your Package” or “Get Your Receipt.” However, in many of these examples, the criminal has copied some parts of a website, which is where the link takes you. At a glance, the website might look real.
The page you are taken to will commonly prompt you for your username, password, and possibly other personally identifiable information such as your name. If you type this information into the site, it is sent to the scammers who will use it for illegal purposes.
Be careful when you receive an email like this example. Instead of interacting with these bad emails, it is always better to contact the company how you usually would.
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------